How to move apple HomePod on different Vlan? The shrewd universe of Web of-Things (IoT) gadgets is truly developing. From ordinary lights to the sprinkler out front, practically every home device and utility has a brilliant partner. For instance, my shrewd home is completely Apple HomeKit viable and comprises of a Shade span with lights, Lutron Caseta savvy dimmers/switches.
Eve Water outside water hose control, iSmartGate carport entryway opener, Schlage deadbolt, Eve movement sensor, Sonos speakers all through the house, a Vocolinc oil diffuser, Vocolionc plug extension, a couple iRobot Roomba vacuum cleaners, some Vocolinc pluggable power source.
An Ecobee indoor regulator to supplant every simple indoor regulator in the house, and a Unifi G4 Doorbell (the doorbell isn't in fact viable with HomeKit, yet I added help with an outsider device known as "Homebridge"). On top of this multitude of savvy home gadgets, I have a modest bunch of other Unifi Safeguard cameras around my property.
Assuming you're understanding this, you might not have very that numerous gadgets, but rather you are presumably either hoping to put resources into a few savvy home gadgets or you have previously begun the method involved with changing your home over completely to the universe of IoT. One way or another.
How to Move Apple Homepod on Different Vlan?
It is critical to consider the security ramifications of adding these gadgets to your organization. For instance, a few shrewd switches have such unfortunate encryption that they are handily compromised and can be overwhelmed to burst into flames.
Read Also: Amazon Echo Gen 4 vs Apple HomePod Mini
While none of the gadgets in my home have this kind of weakness that has been plugged, the chance exists in any case that these gadgets could be utilized by detestable entertainers to create commotion in my home or endeavor to get close enough to different gadgets on my organization.
IoT gadgets keep on further developing their security instruments (for the most part), and IoT is positively not disappearing at any point in the near future. Along these lines, reasonable clients, similar to you, ought to consider how to best safeguard their interior assets. One suggested strategy for getting your organization containing IoT gadgets is to fragment your organization with VLANs.
I will tell you the best way to section your home organization from your IoT gadgets with VLANs, including how to make subnets, VLANs, firewall rules, and how to empower IPS/IDS just in case. To track, your organization should be contained Unifi organizing gear.
My entryway and Unifi regulator is the Unifi Dream Machine Master, however you could utilize any Unifi passage + regulator mix. Also, numerous other organization suppliers other than Unifi will have comparative usefulness, and you can probably achieve a portion of these errands with other stuff.
Making Vlans and Fragmenting the Organization
The initial step is making a VLAN for your IoT organization. The most straightforward method for achieving this undertaking is to make a new subnet for your IoT organization.
For instance, on the off chance that you as of now have a solitary organization for all of your Web associated gadgets, including your PCs, telephones, and so on, you presumably have a solitary subnet that looks something like this: 192.168.1.1/24.
Read Also: The 5 Best Apple Speakers of 2024 Reviews
This is seen on your Unifi Regulator by going to Settings > Organizations (on the old GUI). I suggest you next click "Make New Organization," and name the organization something like "IoT". Explicitly select "Corporate" for the "Reason." It makes it simple to recall whether you set the Passage IP/Subnet 1 number off from your default organization (e.g., set it to something like 192.168.2.1/24 or 192.168.10.1/24).
Beneath, you will see my settings. Notice my Entryway is 10.100.1.1. My default subnet is 10.100.0.1, interestingly. For effortlessness, I have IGMP sneaking around and UPNP empowered. This could assist with bringing down the street for specific shrewd parts like Home Aide.
For VLAN, set any number from 2-4018. I set my DHCP reach to just incorporate x.101-x.254 on the grounds that I needed to hold the initial 100 IPs in this subnet for static tending to. Assuming you maintain that every one of your gadgets should be DHCP, you don't have to adjust this choice. Feel free to save this organization.
Setting up the Remote
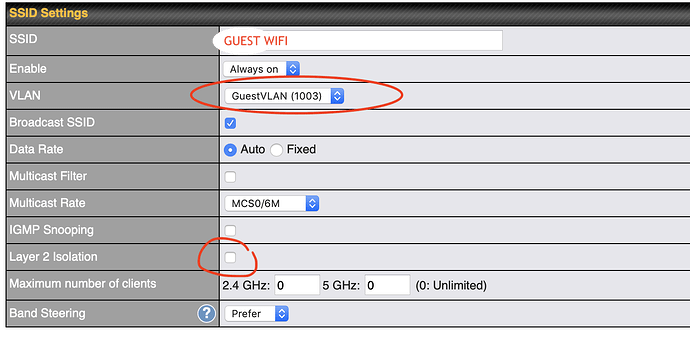
Since most IoT gadgets are remote, you should make a remote SSID for all of your IoT gadgets to interface with independently from the remainder of your home organization. Go to Settings - > Remote Organizations, and snap "Make New Remote Organization."
Name the SSID something paramount, and set the security to "WPA Individual" (old GUI… the new GUI might permit you to explicitly pick WPA2, in which case, do that). For "Organization," pick the subnet/VLAN you made in the past step. This will relate the new SSID to that specific organization portion.
Go on through the arrangement screen to "Cutting edge Choices." Here, I explicitly have Just 2.4GHz empowered for WiFi Groups in light of the fact that most IoT gadgets still just utilize 2.4GHz. Assuming you end up having some 5GHz IoT gadgets, the somewhat better presentation for those gadgets will probably be eclipsed by the steady detaching of your gadgets when both 2.4GHz and 5GHz are empowered at the same time.
IoT gadgets overall do a quite terrible occupation of taking care of Unifi APs with the two groups empowered. Go ahead and take a stab at empowering the two groups in your current circumstance, yet on the off chance that you dislike network and the scandalous "No Reaction" message on Apple HomeKit, I prescribe again to stay with only 2.4GHz for the present.
Debilitate all of Unifi's "BETA" labeled choices like Quick Wandering, as these will likewise cause execution and network issues. I likewise keep my SSID from being communicated to tidy up the WiFi experience for clients at home. It is significantly more pleasant to just see my LAN and my visitor networks being communicated.
This will, in any case, force an additional step when you attempt to add gadgets to HomeKit, as you should interface your telephone to the IoT WiFi prior to adding the IoT gadgets to that organization. Physically adding the SSID can be dreary, yet it is definitely justified as I would like to think once the general arrangement is finished.
I leave GTK rekeying to 3600 seconds. I likewise have a Client Gathering arrangement for IoT gadgets in the event that I need to choke IoT later on. Check to Empower multicast upgrade (IGMPv3). Leave all the other things with no guarantees, and you're done with the Remote arrangement.
Impeding Traffic Between Subnets/VLANs
The following piece of this interaction will set up the Firewall to hinder traffic between the subnets/VLANs. Go to Settings > Directing and Firewall > Firewall. I will accept you are just utilizing IPv4, and we will accordingly just glance at IPv4 rules.
For an itemized meaning of the WAN IN, WAN OUT, WAN Nearby, and so on choices, I will suggest you search the Web. This part can be really confounding, and the meaning of these choices is outside the extent of this post. We will zero in on LAN IN and LAN Nearby for our motivations.
LAN IN
This piece can get confounded relying upon how explicit you need to be with remittances of gadgets between these organization sections. I have many home computerization programs running like HomeBridge and Home Colleague.
I likewise have Sonos speakers, which need their own standards to work appropriately with your iPhone on an alternate subnet. Assuming you have some IoT gadgets (no Sonos) with next to no outside programs like HomeBridge, the main guidelines you should fret about are 2003 and 2012.
How about we take a gander at the referenced Rule 2003. Feel free to make a standard in the LAN IN segment. In the picture beneath, you can see my settings for this standard. Basically, this standard permits your gadgets in your default organization to speak with your IoT gadgets just (traffic stream LAN - > IoT). Match your settings to the settings underneath. Be certain Activity is set to Acknowledge.
Then, how about we look at Rule 2012. Make another standard and match to the picture underneath. Note that Activity Is set to Drop. Additionally, note the States that are checked are New and Invalid. This keeps traffic from moving from the Source (IoT) to Objective (LAN) (traffic stream IoT - >X LAN) in view of the situation with the traffic. Just settled and related traffic will be permitted, then, at that point.
Final Thoughts
That's it! You presently have a completely useful HomeKit arrangement empowered with additional security practices to keep underhandedness from inadequately got IoT gadgets arriving at your inner LAN. It is clear this doesn't moderate 100 percent of the gamble since we're permitting traffic to stream in inverse course.
You can lock your subnets down much more by exploring different avenues regarding completely obstructing your traffic from your LAN to your IoT network yet Just permitting rather your HomeKit regulator (e.g., Apple television, Homepod, and so forth.).
These guidelines can and presumably ought to be changed to accommodate your current circumstance, yet the principles depicted above will basically kick you off.
